Macros are disabled by default because they can be vectors for malicious code such as viruses or other exploits. Excel protects the end user from these harmful pieces of code by disabling the questionable content altogether when a macro-enabled workbook is opened.
As we discussed earlier, disabling of macro content does not affect the ability to edit data; it just affects running macros on the data. In Office 2016, data is always available even if macro content is disabled.
We will discuss macro security settings later, but for now, let's go ahead and enable this content and continue.
Step1. To enable the macro content,
Click
NOTE for MacOS Users: To enable the macro content, Click
NOTE: Be careful when enabling content because the content might contain macros that could contain viruses. Be certain to regularly scan your computer with a recently updated version of anti-virus software, and to keep the virus definitions for that software updated regularly, as well.
Best Practices in Macro Security
We have been discussing how to protect our machines from malicious macro code, but what makes macro code malicious and what are some behaviors that can minimize the risk of being victimized by a macro?
Examples of Macro Viruses
The first Excel macro virus was called ExcelMacro/Laroux, or Laroux for short. It consisted of an auto_open macro and a macro called check_files. When the workbook was opened, it would look for an occurrence of the Personal Macro Workbook. If none was found, it would create one and copy itself to the workbook. Laroux would then copy itself to every workbook created from that point forward, infecting every file created on a specific machine.
Another popular macro-driven virus was W97M.Melissa, or Melissa for short. This virus started making its rounds in the late 90s/early 2000s. Melissa infected Microsoft Word, disabling the application's default macro detection. After infecting Word, it would use Outlook or Outlook Express to mail itself to the first 50 people in each address book. It also added itself, much like Laroux did, to each file created in Word from then on, making its spread quite rapid. When this virus was initially introduced, it was known for bringing mail servers and company intranets down under massive demands on the networks' bandwidth.
It may seem like these viruses are so old that mentioning them makes the content of this workshop outdated. The reality is that both of these viruses are still in use today as a method of delivering a more sophisticated malware payload. For example, someone with malicious intent can use Laroux as an entry point into an unsecured machine and then propogate the spread of some other, more sophisticated, or more malicious virus by making a few changes to the macro's code. The piggybacking malware doesn't need to be a macro, but could be a standalone program.
Protecting Your Computer from Macro Viruses
There are a few behaviors that can be modified to better protect yourself from malicious macros.
The following list outlines these behaviors in more detail.
- Avoid implicit trust—The notion of trusting a publisher is one of the key ways to protect yourself from malicious macros. If you receive a file from someone you don't know that contains a macro, chances are it is not a safe macro. These macros should not be run without great care being taken to protect yourself.
- Don't trust "surprise files"—When you receive a file from a colleague that contains macros, it shouldn't be a surprise. You should already have an idea that the file is coming and it should appear to be for a legitimate purpose. If you receive a file that you are not expecting, it is best to be suspicious of its content until it can be verified in a separate message.
- Do not enable questionable content—Probably the best advice to protect yourself from macro-virus infection is to not enable questionable content, especially if the file is questionable. Microsoft Office 2016 allows the data in a file to be manipulated without enabling possibly malicious content and in most cases, the content is what is being shared, not the automation built into the file.
The bottom line to protect yourself is to question the validity of macro-enabled files sent to you and always verify that the file is intended to be sent to you. As we learned in the Melissa example, a macro virus can use other applications to propagate itself via email or other means.
For more information about macro security, visit the IU Knowledge Base.
Let's explore the settings on both Windows and MacOS that can help protect us from malicious code.
NOTE for MacOS Users: Skip foward to the heading, "Using Security & Privacy Settings on MacOS".
Using the Trust Center on Windows
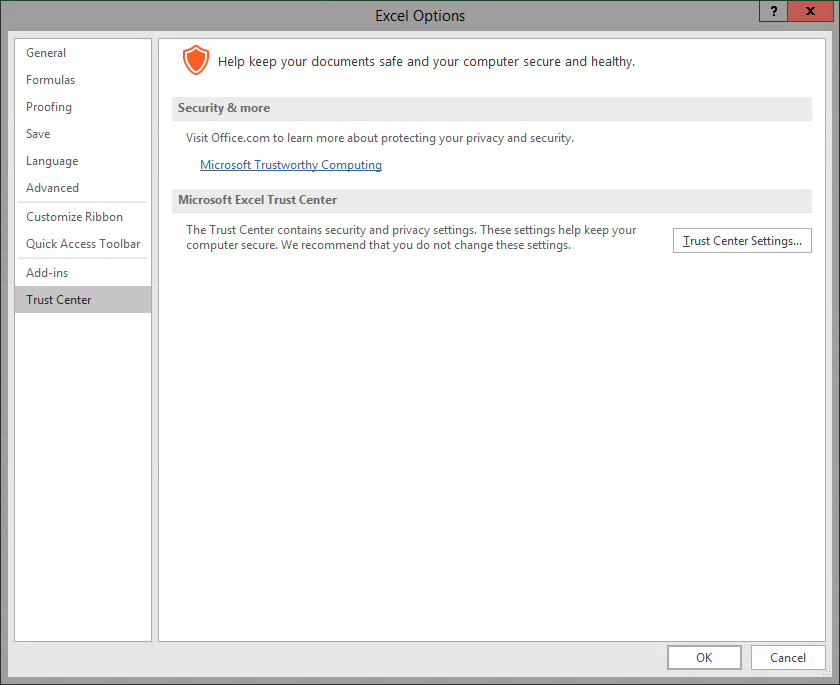
Macro security in Office 2016 is controlled by a group of settings called the Trust Center. The Trust Center allows us as an end user to specify who we trust as publishers and which directories contain trusted files. When opening a file in a trusted location or from a trusted source, Excel will not disable any content and will not even prompt to have the content disabled.
Let's explore the Trust Center now.
Step1. To open Excel Options,
Click File, Click
Step2. To access the Trust Center, in the navigation pane,
Click Trust Center
Step3. To view the Trust Center Settings,
Click
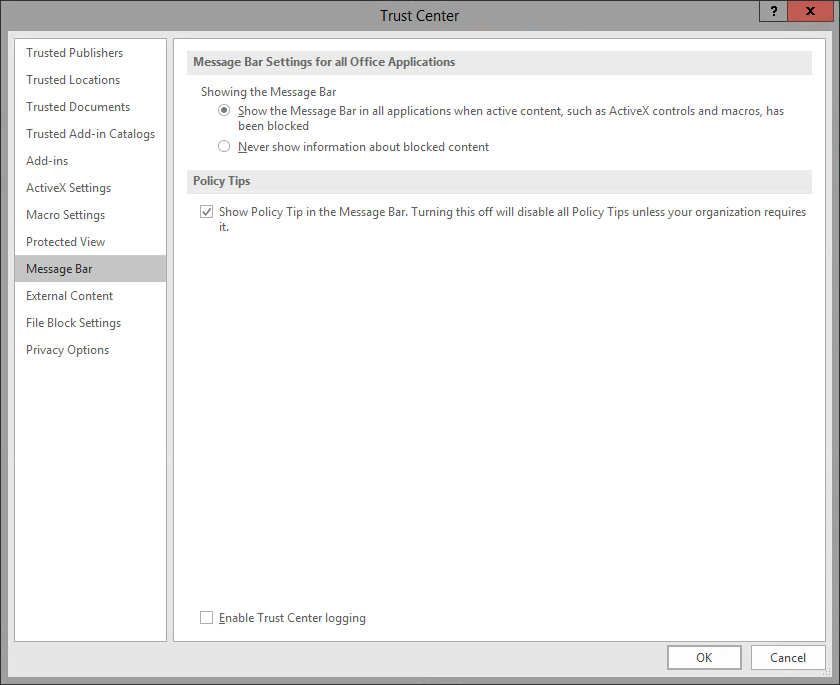
NOTE: Your screen may look slightly different depending on the last section that has been viewed on your machine.
| Section | Description |
|---|---|
| Trusted Publishers | Trusted publishers are developers who create macro, ActiveX, or add-in content for Excel. Content from trusted publishers will be signed with a valid digital signature. For more information see Excel's online help. |
| Trusted Locations | Trusted locations are folders on your hard drive or any network drive where you place content you know to be from a trusted source. Any file placed in a trusted location will be opened without being checked by the Trust Center. |
| Trusted Documents | Trusted documents are documents that have been opened previously and their macro content was enabled. If you opened a document in error, you can clear the list here. |
| Trusted App Catalog | Trusted app catalogs are trusted locations on a SharePoint site. Use the settings in this section to identify catalogs that contain only documents from trusted sources. |
| Add-ins | Add-ins settings allow the user to designate whether or not add-ins must be signed by a trusted publisher. It also contains an option to disable all application add-ins. |
| ActiveX Settings | ActiveX Settings allow the user to set how he/she would like the application to handle ActiveX controls. |
| Macro Settings | Macro settings allow the user to designate which macros should be enabled by default in certain files. |
| Protected View | Allows files from potentially unsafe locations to be opened, inspected, and reviewed while minimizing risk to your machine. |
| Message Bar | Message Bar determines whether or not the Message Bar is shown when questionable content is present. |
| External Content | External Content controls how Excel handles connections to external data or external workbooks. |
| File Block Settings | Prevents out-dated documents from opening and can cause a file to be opened in Protected View. Opening some of these formats can cause your machine to be vulnerable to attacks. |
| Privacy Options | Privacy Options control how Excel connects to online help and how the online help content is managed. It also allows the user to remove personal data from files when they are saved. |
Step4. To exit the Trust Center,
Click , Click
, Click
Using Security & Privacy Settings on MacOS
On MacOS, Office 2016 applications have been sand-boxed, which means that Excel is restricted from accessing resources outside the application container. For more information about macros security for Office 2016 on MacOS, visit the Microsoft Developer Network's page about Office for Mac.
Step1. To review the security and privacy settings on MacOS,
Click Excel, Click Preferences...
Step2. To see Security and Privacy settings,
Click
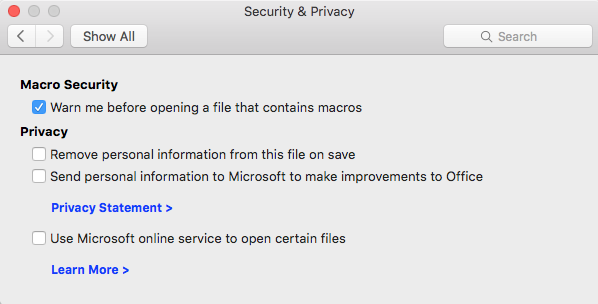
Step3. Make sure the button "Warn me before opening a file that contains macros" is selected.
Step4. Close the window.

